- Joined
- Jul 27, 2018
Hello everyone,
As some of you may know, I've made Shenmue I & II 16:9 Generic Hex Fix v1, an easy one click visual solution for windows to permanently patch Shenmue.exe and Shenmue2.exe based on @Esppiral's hard work and findings.
The only reason for making those patchers, has been to allow everyone to enjoy those findings as quickly, easily and hassle-free as possible, but like "any" file patchers that make permanent changes to an executable file, those can be detected by some AV software kits and flagged as false positives.
More advanced security kits, however, use more advanced analysis and they don't flag such patchers. Windows Defender is one of the more basic kits so it works on a basic level, and although it's more common, it isn't as accurate as the more advanced solutions out there so it may flag the patchers as false positive.
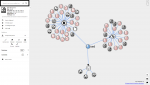
Here's an analysis for the latest Shenmue and Shenmue2 v2 patchers from www.virustotal.com.


There will be at least another patch for Shenmue I & II landing sometimes next week, and probably the Generic Hex Fix patchers will need a compatibility update for the upcoming version of Shenmue and/or Shenmue II.
Although the patchers are perfectly safe, I realise that some might be concerned or maybe not fully aware of false positive flagging. Therefore, I want your opinion on what I should do with the patchers for now and the near future.
I'm thinking of four possible scenarios :
As some of you may know, I've made Shenmue I & II 16:9 Generic Hex Fix v1, an easy one click visual solution for windows to permanently patch Shenmue.exe and Shenmue2.exe based on @Esppiral's hard work and findings.
The only reason for making those patchers, has been to allow everyone to enjoy those findings as quickly, easily and hassle-free as possible, but like "any" file patchers that make permanent changes to an executable file, those can be detected by some AV software kits and flagged as false positives.
From pcworld.comFalse positive detections are common in the antivirus industry.They occur when a benign program is wrongfully flagged as malicious due to an overly broad detection signature or algorithm used in an antivirus product.
More advanced security kits, however, use more advanced analysis and they don't flag such patchers. Windows Defender is one of the more basic kits so it works on a basic level, and although it's more common, it isn't as accurate as the more advanced solutions out there so it may flag the patchers as false positive.
Here's an analysis for the latest Shenmue and Shenmue2 v2 patchers from www.virustotal.com.


There will be at least another patch for Shenmue I & II landing sometimes next week, and probably the Generic Hex Fix patchers will need a compatibility update for the upcoming version of Shenmue and/or Shenmue II.
Although the patchers are perfectly safe, I realise that some might be concerned or maybe not fully aware of false positive flagging. Therefore, I want your opinion on what I should do with the patchers for now and the near future.
I'm thinking of four possible scenarios :
- Keep making them as an easy to use, flexible and more compatible patching solution.
- Take the patchers down, and distribute individual patches using Lunar IPS, which is a less flexible yet simple solution that has been in use for years.
- Take the patchers down, and use another patching solution of your suggestion.
- Take the patchers down, and stop making patches / patchers, they're not needed anymore.
Last edited: